© 2024 borui. All rights reserved.
This content may be freely reproduced, displayed, modified, or distributed with proper attribution to borui and a link to the article:
borui(2024-01-29 19:43:26 +0000). What is CORS policy. https://borui/blog/2024-01-29-en-what-is-cors.
@misc{
borui2024,
author = {borui},
title = {What is CORS policy},
year = {2024},
publisher = {borui's blog},
journal = {borui's blog},
url={https://borui/blog/2024-01-29-en-what-is-cors}
}What is same origin policy and what does it do
The same-origin policy is a critical security mechanism that restricts how a document or script loaded by one origin can interact with a resource from another origin.
The same-origin policy mitigates an attack known as Cross-Site-Request-Forgery (XSRF, CSRF).
What does CORS do?
According to same origin policy, no cross-origin access is allowed.
That's why we use CORS to allow cross-origin access. CORS is a part of HTTP that lets servers specify any other hosts from which a browser should permit loading of content.
📓 Note: CORS is what allows cross-origin access. On the contrary, poorly implemented cors rules will increase risk of csrf attack, not prevent it. A common way to prevent csrf is to use csrf token.
📓 Note: Another way to allow cross-origin access is jsonp, that's using the fact that some sataic resource tags like
<script><img>are allowed by defalut.
In light of the risk CORS introduces, preflighted request is introduced to cope with this issue.
what is preflighted request
Some requests don't trigger a CORS preflight. Those are called simple requests from the obsolete CORS spec, though the Fetch spec (which now defines CORS) doesn't use that term.
A simple request is one that meets all the following conditions:
One of the allowed methods: GET, HEAD, POST
Headers: Accept, Accept-Language, Content-Language, etc.
Content-Type headers: application/x-www-form-urlencoded, multipart/form-data, text/plain, etc.
...
(Full detailed specificcations see mdn docs or web standards)
Unlike simple requests, for "preflighted" requests the browser first sends an HTTP request using the OPTIONS method to the resource on the other origin, in order to determine if the actual request is safe to send. Such cross-origin requests are preflighted since they may have implications for user data.
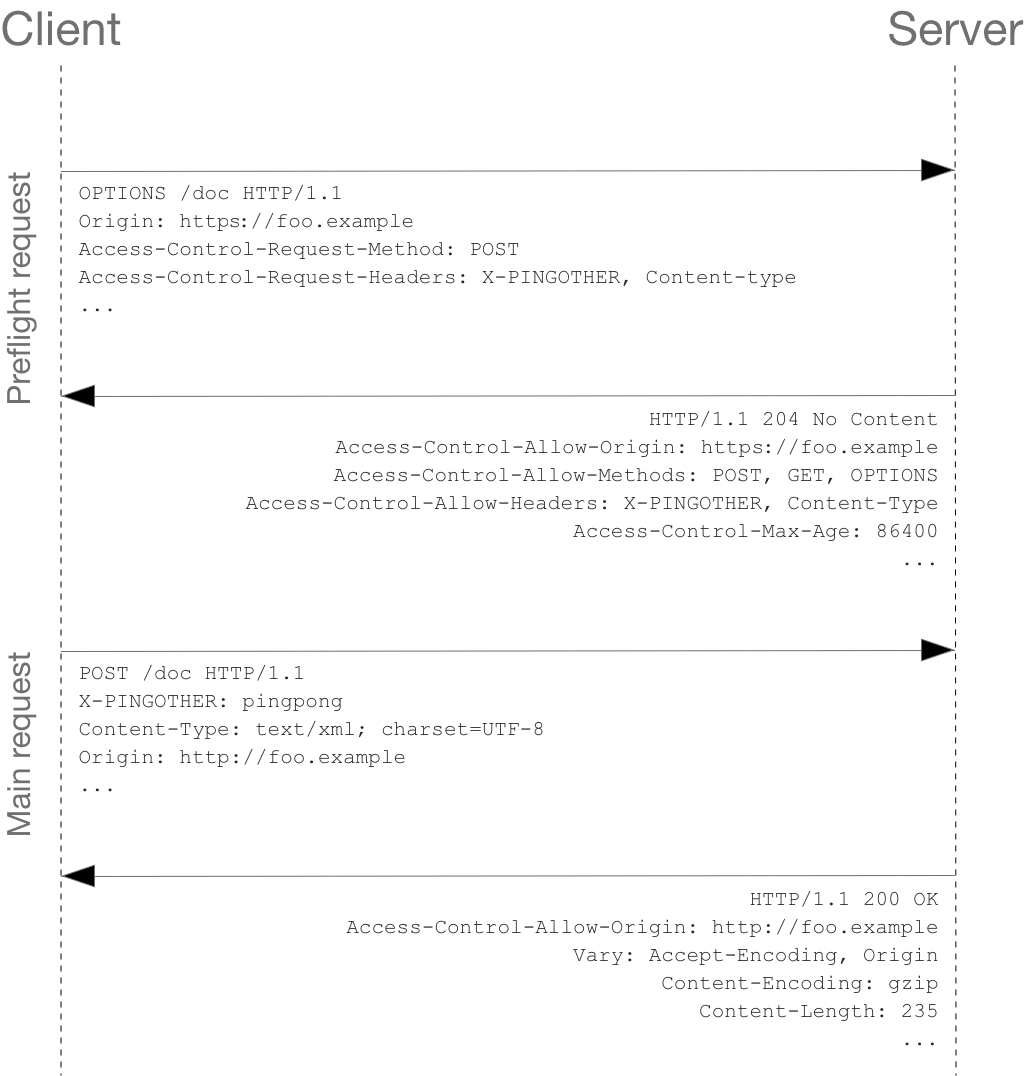
The intention of preflight request is largly to block requests that modify resources on the server [PUT, POST, DELETE]. Requests first create a sample request to the server to check which methods allowed in the server and then communicates to the client (your web browser). This Sample request is called Preflight.
For example, a hacker website initiates a PUT request with the purpose of clearing the victim user's account balance to zero. The browser will first do a preflight and find that the received response does not carry a CORS response header, so the actual PUT request will not be sent. If the actual request was sent with user's credential stored in cookie, and the server took the request with no further filtering, then the hacker would succeed.
📓 Note: SameSite cookies is a new way to prevent csrf.
Relevant Reading
-
Same-origin policy. (n.d.). MDN docs. Retrieved January 29, 2024, from https://developer.mozilla.org/en-US/docs/Web/Security/Same-origin_policy
-
Cross-Origin Resource Sharing (CORS)#Preflighted requests. (n.d.). MDN docs. Retrieved January 29, 2024, from https://developer.mozilla.org/en-US/docs/Web/HTTP/CORS
-
双猫CC. (5 Jan, 2022.). 循序渐进理解:跨源跨域,再到 XSS 和 CSRF. [Blog post]. Retrieved January 29, 2024, from https://catcat.cc/post/2020-06-23/
-
Altynai Baitulakova. (19 dec, 2022.). Web Security: an Overview of SOP, CORS, and CSRF. Mad Devs. [Blog post]. Retrieved January 29, 2024, from https://maddevs.io/blog/web-security-an-overview-of-sop-cors-and-csrf/